Note: Descriptions are shown in the official language in which they were submitted.
CA 02895597 2015-06-29
Secure Off-Line Password Generation and Recall Device
This invention provides a portable device to enable users to generate, and
later recall, highly-secure
passwords which are unique to them and each device; including the simple
generation of passwords
which change or rotate at designated time intervals such as is mandated by
many corporate security
policies.
Background Of The Invention
As more and more of peoples' activities take place online, the number of
distinct accounts for which
one must maintain credentials has increased dramatically in recent years. The
threshold for what is
considered a secure password constantly increases. In the early 21s' century a
password of at least 8
characters, consisting of letters and digits, was considered sufficient. In
the second decade of the 21s'
century, this requirement has become inadequate, and many websites and
internal corporate systems
now mandate a password of more than 8 characters, consisting of letters (both
upper- and lower-case),
digits, and punctuation. Passwords consisting mainly of common dictionary
words, or slight
misspellings thereof, are now often rejected by password validation algorithms
as insufficiently secure.
The above increasing restrictions, combined with the sheer number of accounts
for which people must
remember details, has reached distressing levels for many. This causes a
breakdown in password
security, in that many people resort to generating one password fulfilling the
requirements described
above, and re-use this password (or a small number of trivial variations
thereof) across multiple
accounts. This creates a danger both to the individual and to the system being
used: if one system's
network or database is compromised by attackers, those attackers often then
use the passwords gained
in order to attempt to access other common services (such as hosted electronic
mail, banking sites,
gaming accounts, or web forums) in the expectation that the user may have re-
used a password across
these disparate systems. In such situations multiple systems are often
compromised.
Complex systems exist, comprised of electronic dongles, or of software
programs inhabiting a mobile
computing device, which yield an authentication token which changes in
synchrony with a particular
corporate network's password storage server:
1
CA 02895597 2015-06-29
= Method and apparatus for positively identifying an individual US4720860 A
= Multi-factor authentication using a unique identification header (uidh)
US 20130318581 Al
However, these systems require infrastructure external to the device carried
by the user, consisting of a
particular remote computer or network of computers, which must be administered
by one or more staff
within an organization; a method of clock synchronization; and interaction
with said infrastructure that
is explicitly tied to the design of said device. Thus they are tied to the
particular network of said
organization and are not generally usable across multiple organizations as
they do not share a single
account or password database.
The invention herein described addresses these shortcomings, providing a
device and method for
generating and providing unique authentication credentials to a plurality of
users without the need for
any registration with, administration of, or synchronization with, external
systems at minimal cost, and
which can be applied to disparate systems.
Summary Of The Invention
In the drawings, which form the typical physical embodiment of this invention,
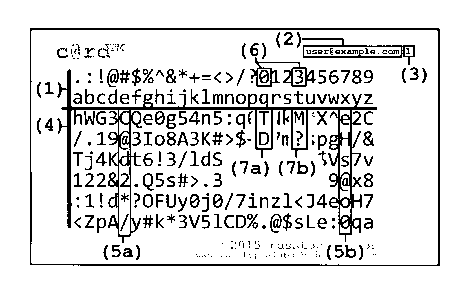
Fig. 1 is a diagram of the functional components of a device produced by the
invention and a typical
layout of one such device, with each functional region of the device labeled
according to its use in the
password generation and recall procedure described below.
Fig. 2 describes quantities not physically rendered on the device, but which
are nevertheless essential
to the production of, and operation of, a particular instance of the device.
In particular, Fig. 2(8)
denotes the algorithm (resident on an issuing authority server) which derives
unique pseudo-random
data based upon keying information (Fig. 1(2,3) and the issuing authority's
identifier Fig. 3(1)), ensures
said data fits specific constraints in order to guarantee strong password
tokens, and arranges and
renders said data into a tabular form onto each unique instance of the device.
Fig. 3 depicts the algorithm, also claimed, which generates the pseudo-random
data in a tabular format
2
CA 02895597 2015-06-29
such as shown in Fig. 1(4)., using the keying information (Fig. 1(2,3) and the
issuing authority's
identifier Fig. 3(1)).
3
CA 02895597 2015-06-29
Detailed Description Of The Invention
In the typical physical embodiment of this invention, each unique instance of
the invention contains a
common header section, Fig. 1(1), a pseudo-randomly generated table, Fig.
1(4), generated by an
algorithm Fig. 2(8), typically implemented within a computer, based upon the
keying identifier prefix,
Fig. 1(2) and suffix, Fig. 1(3), visible on the device, plus an issuer field,
Fig. 3(1); Fig. 1(2) typically,
but not exclusively, consisting of the user's electronic-mail address,
employee ID, or a serial number
identifying the particular instance of the device; Fig. 1(3) typically
consisting of a single integer, but
possibly any unique sequence of symbols (letters, digit or punctuation) which
can be varied amongst
instances of the device without requiring a change to Fig. 1(2); thus allowing
devices to be issued to
the same user to replace a previous device in case of loss or theft. As Fig.
1(2,3) and Fig. 3(1) are
inputs to the algorithm depicted in Fig. 3., residing on the issuing
authority's server, Fig. 2(8), the
pseudo-randomly generated table in Fig. 1(4) may be recreated at will by any
run of the algorithm Fig.
2(8), Fig. 3; or one or both of Fig. 1(2) and Fig. 1(3) may be varied in order
to change the output of
algorithm Fig. 2(8), Fig. 3 to vary the resulting table Fig. 1(4) rendered on
each device instance.
Users possessing an instance of the device choose a sequence, consisting
typically, but not restricted to,
the first 2 characters of the system against which they wish to authenticate,
using this sequence as
indices into the header, Fig. 1(1). In sequence, the user then reads off
symbols in a downward,
columnar fashion (5a), (5b), which are guaranteed by the algorithm to each
contain at least one upper-
case letter, one lower-case letter, one digit, and one punctuation symbol, in
order to derive a sequence
of symbols comprising the portion of an authentication token which is unique
to the system. The user
then optionally proceeds to prepend, append or interpose, at their discretion,
a pre-chosen secret (9),
typically consisting of a word or phrase, in order to provide a second portion
of the authentication
token, which is never stored on the device; this prevents use of the device by
a third-party in order to
gain access to the intended user's account without their knowledge.
Optionally, if authentication
credentials change at predetermined intervals (such as due to a corporate
policy of requiring new
passwords every two months, as an example) the user makes mental note of the
current month
(considering March as month '03' in the example of Fig. 1(6)) at which
authentication credentials must
change, considering each month as a numeric quantity. The header columns thus
chosen such as in Fig.
1(6) are then used to read off additional symbols Fig. 1(7a,7b) in a downward,
columnar fashion,
adding these symbols to the authentication token previously derived by the
composition of Fig.
4
CA 02895597 2015-06-29
1(5a,5b), and (9). In this manner may authentication be updated in synchrony
with required corporate
policies.
The Embodiments Of The Invention In Which An Exclusive Property Or Privilege
Is Claimed
Are Defined As Follows:
1. A pre-assigned issuer field, consisting of a plurality of symbols, used to
distinguish one entity or
organization from another when they create multiple devices which are
instances of the invention, to
prevent unintended generation of identical devices by separate issuers, Fig.
3(1);
2. A keying identifier prefix, consisting of a plurality of symbols, unique to
each user possessing a
device, said prefix located on the surface of the invention, which is linked
uniquely to the user in a
name-like manner at the time of device creation, Fig. 1(2), and combined
combined with the pre-
assigned issuer field in claim 1.;
3. A keying identifier suffix, consisting of a plurality of symbols, Fig.
1(3), unique to each particular
instance of a device possessed by each user, said suffix rendered on the same
surface as claim 2., said
suffix may be varied in order to generate a new, unique instance of the device
while preserving the
keying identifier prefix in claim 2. and the pre-assigned issuer field of
claim 1.;
4. The algorithm, process and/or method depicted in Fig. 3, typically residing
on a server, Fig. 2(8),
typically administered by an issuer identified by claim 1., said algorithm
generating a plurality of
pseudo-random symbols, arranged in a tabular format Fig. 1(4), lying beneath
and aligned with the
heading rendered in Fig. 1(1), on the same surface as Fig. 1(1,2,3); said
algorithm's input comprising
claims 1., 2. and 3., and the algorithm's output guaranteeing a unique
plurality of symbols for a
particular device instance, the columns of said plurality as depicted in Fig.
1(4) each holding the
property that each column contains at least one upper-case letter, at least
one lower-case letter, at least
one digit, and at least one punctuation symbol; such aforementioned property
computed and verified
by the algorithm as shown in Figure 3. Note that the essence of this
algorithm, process and method is
preserved by any equivalent algorithm, process or method which computes the
plurality of symbols
rotated by any angle when impressed upon instances of the generated devices
(for example, but not as
the sole example, swapping rows and columns leaves the essential nature and
utility of a resulting
CA 02895597 2015-06-29
instance of a device unchanged);
5. Each unique device instance, typically, but not exclusively, comprised of a
portable sheet or card,
upon which are rendered Fig. 1(1,2,3,4), generation of which is described in
claims 1., 2., 3. and 4.
Device instances can be equivalently manifested on any object which can take
an impression, including
but not limited to pendants, keychains, wallets, notebook covers and so on.
6. The algorithm, process and/or method, performed by a user, either manually
or with assistance of
further devices not claimed herein, of generating and retrieving a string from
the unique device from
claim 5., which is comprised of, generated by and described in claims 1., 2.,
3. and 4., said string to be
used as a unique authentication token comprised of column choices Fig.
1(5a,5b), said column choices
being determined from some combination (at user's discretion) of the letters,
digits or symbols
comprising the name of the system to which the user is attempting to
authenticate Fig. 2(10);
additionally and optionally using a week or month value to drive a choice of
additional header column
choices, Fig. 1(6), which are in turn used to derive partial computed column
choices Fig. 1(7a,7b); and
finally combining the aforementioned column choices in series ¨ Fig. 1(5a,5b)
and optionally, partial
column choices Fig. 1(7a,7b) ¨ with a user-memorized phrase Fig. 2(9) to
derive a complete
authentication token which is unique to the aforementioned system Fig. 2(10)
for said user.
7. The system, as a whole, for defining issuers as described in claim 1.,
generating unique sets of
keying identifiers as described in claims 1., 2., and 3., inputting said
keying identifiers into a
computing device such as depicted in Fig. 2(8) and implementing the algorithm,
process and/or method
of claim 4., applying said algorithm, process and/or method's output to the
creation of a plurality of
device instances as described in claim 5. for distribution to users in order
to enable said users to
generate and recall unique authentication tokens (passwords) using the
algorithm, process and/or
method of claim 6.
Drawings
Figure 1.
Figure 2.
Figure 3.
6
CA 02895597 2015-06-29
System for Production, Distribution and Use of Secure Off-Line Password
Generation and Recall Devices
Russell L. Magee
131 2"d Ave. SE High River, AB T1V 1G7 Canada
rmagee@gmail.com
1
CA 02895597 2015-06-29
System for Production, Distribution and Use of Secure Off-Line Password
Generation and Recall Devices
Computer Security/Electronic Authentication/Information Technology
Russell L. Magee
131 2 Ave. SE High River, AB T1V 1G7 Canada
rmagee0gmai1.com
Abstract Of The Disclosure
The invention provides a physical device which enables generation and recall
of unique, secure
authentication tokens (passwords) for a plurality of computer accounts for a
single identity (user or
group). Furthermore, an algorithm and method for producing any number of such
physical devices,
each unique to a user or group, is provided. The device typically consists of
a printed card with a
keying identifier composed of an issuing authority, user identity and issue
number, which is used to
generate the unique-per-device random data set, which is arranged into a
tabular form beneath a
heading which consists of all common characters (letters, digits and common
punctuation) which may
occur in the name or location of computer account. The heading is consulted
based upon some subset
of the characters consisting of the computer account which is to be accessed
(for example, but not
restricted to, the initial 2 characters of the account, being the domain name
of a web site, the name of a
company or a company's internal network/domain name); characters are read in a
downward columnar
sequence from the chosen header columns, yielding a sequence of characters;
which when combined
with a user-memorized passphrase or word(s), further yields a unique per-user,
per-device password for
the account in question. To derive passwords which update or rotate
sequentially in time (such as a bi-
monthly password change mandated by a company's security policies), the
aforementioned procedure
is combined with the further step of encoding the current month, as a two-
digit number with a leading
zero ranging from 01 (January to 12 (December), or abbreviation (jan/feb/mar/
etc.) or other scheme,
and using this encoding as a lookup into the aforementioned header to take
additional characters, again
read in a downward columnar sequence, to create a time-dependent password
suffix. The
aforementioned keying identifier printed on the device allows re-issue of a
duplicate card in the case of
loss, or in the case of theft, generation of a new card with a differing
random data set, accomplished by
2
CA 02895597 2015-06-29
either changing the user identity or incrementing the issue number portion of
said keying identifier.
Secure Off-Line Password Generation and Recall Device
This invention provides a portable device to enable users to generate, and
later recall, highly-secure
passwords which are unique to them and each device; including the simple
generation of passwords
which change or rotate at designated time intervals such as is mandated by
many corporate security
policies.
Background Of The Invention
As more and more of peoples' activities take place online, the number of
distinct accounts for which
one must maintain credentials has increased dramatically in recent years. The
threshold for what is
considered a secure password constantly increases. In the early 21" century a
password of at least 8
characters, consisting of letters and digits, was considered sufficient. In
the second decade of the 21"
century, this requirement has become inadequate, and many websites and
internal corporate systems
now mandate a password of more than 8 characters, consisting of letters (both
upper- and lower-case),
digits, and punctuation. Passwords consisting mainly of common dictionary
words, or slight
misspellings thereof, are now often rejected by password validation algorithms
as insufficiently secure.
The above increasing restrictions, combined with the sheer number of accounts
for which people must
remember details, has reached distressing levels for many. This causes a
breakdown in password
security, in that many people resort to generating one password fulfilling the
requirements described
above, and re-use this password (or a small number of trivial variations
thereof) across multiple
accounts. This creates a danger both to the individual and to the system being
used: if one system's
network or database is compromised by attackers, those attackers often then
use the passwords gained
in order to attempt to access other common services (such as hosted electronic
mail, banking sites,
gaming accounts, or web forums) in the expectation that the user may have re-
used a password across
these disparate systems. In such situations multiple systems are often
compromised.
Complex systems exist, comprised of electronic dongles, or of software
programs inhabiting a mobile
computing device, which yield an authentication token which changes in
synchrony with a particular
3
CA 02895597 2015-06-29
corporate network's password storage server:
= Method and apparatus for positively identifying an individual US4720860 A
= Multi-factor authentication using a unique identification header (uidh)
US 20130318581 Al
However, these systems require infrastructure external to the device carried
by the user, consisting of a
particular remote computer or network of computers, which must be administered
by one or more staff
within an organization; a method of clock synchronization; and interaction
with said infrastructure that
is explicitly tied to the design of said device. Thus they are tied to the
particular network of said
organization and are not generally usable across multiple organizations as
they do not share a single
account or password database.
The invention herein described addresses these shortcomings, providing a
device and method for
generating and providing unique authentication credentials to a plurality of
users without the need for
any registration with, administration of, or synchronization with, external
systems at minimal cost, and
which can be applied to disparate systems.
Summary Of The Invention
In the drawings, which form the typical physical embodiment of this invention,
Fig. 1 is a diagram of the functional components of a device produced by the
invention and a typical
layout of one such device, with each functional region of the device labeled
according to its use in the
password generation and recall procedure described below.
Fig. 2 describes quantities not physically rendered on the device, but which
are nevertheless essential
to the production of, and operation of, a particular instance of the device.
In particular, Fig. 2(8)
denotes the algorithm (resident on an issuing authority server) which derives
unique pseudo-random
data based upon keying information (Fig. 1(2,3) and the issuing authority's
identifier Fig. 3(1)), ensures
said data fits specific constraints in order to guarantee strong password
tokens, and arranges and
renders said data into a tabular form onto each unique instance of the device.
4
CA 02895597 2015-06-29
Fig. 3 depicts the algorithm, also claimed, which generates the pseudo-random
data in a tabular format
such as shown in Fig. 1(4)., using the keying information (Fig. 1(2,3) and the
issuing authority's
identifier Fig. 3(1)).
=
CA 02895597 2015-06-29
=
Detailed Description Of The Invention
In the typical physical embodiment of this invention, each unique instance of
the invention contains a
common header section, Fig. 1(1), a pseudo-randomly generated table, Fig.
1(4), generated by an
algorithm Fig. 2(8), typically implemented within a computer, based upon the
keying identifier prefix,
Fig. 1(2) and suffix, Fig. 1(3), visible on the device, plus an issuer field,
Fig. 3(1); Fig. 1(2) typically,
but not exclusively, consisting of the user's electronic-mail address,
employee ID, or a serial number
identifying the particular instance of the device; Fig. 1(3) typically
consisting of a single integer, but
possibly any unique sequence of symbols (letters, digit or punctuation) which
can be varied amongst
instances of the device without requiring a change to Fig. 1(2); thus allowing
devices to be issued to
the same user to replace a previous device in case of loss or theft. As Fig.
1(2,3) and Fig. 3(1) are
inputs to the algorithm depicted in Fig. 3., residing on the issuing
authority's server, Fig. 2(8), the
pseudo-randomly generated table in Fig. 1(4) may be recreated at will by any
run of the algorithm Fig.
2(8), Fig. 3; or one or both of Fig. 1(2) and Fig. 1(3) may be varied in order
to change the output of
algorithm Fig. 2(8), Fig. 3 to vary the resulting table Fig. 1(4) rendered on
each device instance.
Users possessing an instance of the device choose a sequence, consisting
typically, but not restricted to,
the first 2 characters of the system against which they wish to authenticate,
using this sequence as
indices into the header, Fig. 1(1). In sequence, the user then reads off
symbols in a downward,
columnar fashion (5a), (5b), which are guaranteed by the algorithm to each
contain at least one upper-
case letter, one lower-case letter, one digit, and one punctuation symbol, in
order to derive a sequence
of symbols comprising the portion of an authentication token which is unique
to the system. The user
then optionally proceeds to prepend, append or interpose, at their discretion,
a pre-chosen secret (9),
typically consisting of a word or phrase, in order to provide a second portion
of the authentication
token, which is never stored on the device; this prevents use of the device by
a third-party in order to
gain access to the intended user's account without their knowledge.
Optionally, if authentication
credentials change at predetermined intervals (such as due to a corporate
policy of requiring new
passwords every two months, as an example) the user makes mental note of the
current month
(considering March as month '03' in the example of Fig. 1(6)) at which
authentication credentials must
change, considering each month as a numeric quantity. The header columns thus
chosen such as in Fig.
1(6) are then used to read off additional symbols Fig. 1(7a,7b) in a downward,
columnar fashion,
adding these symbols to the authentication token previously derived by the
composition of Fig.
6
CA 02895597 2015-06-29
1(5a,5b), and (9). In this manner may authentication be updated in synchrony
with required corporate
policies.
The Embodiments Of The Invention In Which An Exclusive Property Or Privilege
Is Claimed
Are Defined As Follows:
1. A pre-assigned issuer field, consisting of a plurality of symbols, used to
distinguish one entity or
organization from another when they create multiple devices which are
instances of the invention, to
prevent unintended generation of identical devices by separate issuers, Fig.
3(1);
2. A keying identifier prefix, consisting of a plurality of symbols, unique to
each user possessing a
device, said prefix located on the surface of the invention, which is linked
uniquely to the user in a
name-like manner at the time of device creation, Fig. 1(2), and combined
combined with the pre-
assigned issuer field in claim 1.;
3. A keying identifier suffix, consisting of a plurality of symbols, Fig.
1(3), unique to each particular
instance of a device possessed by each user, said suffix rendered on the same
surface as claim 2., said
suffix may be varied in order to generate a new, unique instance of the device
while preserving the
keying identifier prefix in claim 2. and the pre-assigned issuer field of
claim 1.;
4. The algorithm, process and/or method depicted in Fig. 3, typically residing
on a server, Fig. 2(8),
typically administered by an issuer identified by claim 1., said algorithm
generating a plurality of
pseudo-random symbols, arranged in a tabular format Fig. 1(4), lying beneath
and aligned with the
heading rendered in Fig. 1(1), on the same surface as Fig. 1(1,2,3); said
algorithm's input comprising
claims 1., 2. and 3., and the algorithm's output guaranteeing a unique
plurality of symbols for a
particular device instance, the columns of said plurality as depicted in Fig.
1(4) each holding the
property that each column contains at least one upper-case letter, at least
one lower-case letter, at least
one digit, and at least one punctuation symbol; such aforementioned property
computed and verified
by the algorithm as shown in Figure 3. Note that the essence of this
algorithm, process and method is
preserved by any equivalent algorithm, process or method which computes the
plurality of symbols
rotated by any angle when impressed upon instances of the generated devices
(for example, but not as
the sole example, swapping rows and columns leaves the essential nature and
utility of a resulting
7